24+ Free Security Risk Assessment Templates – Simple PDF, MS Word
A security risk assessment template is a document that outlines the steps and processes for conducting a comprehensive evaluation of various security threats. Its purpose is to identify possible risks, the consequences of those risks, and recommend strategies to mitigate or reduce them.
This type of assessment allows organizations to proactively manage security risks through preventive measures such as implementing strong authentication protocols, setting access control restrictions, and investing in user awareness campaigns. By properly utilizing a security risk assessment template and conducting regular assessments, businesses can ensure that their operations are well-protected from malicious attacks or weakly secured systems.
Download Free Security Risk Assessment Templates
Importance of Conducting Security Risk Assessments
Security risk assessments are critical components of any organization’s digital security efforts. They provide insight that most IT teams and security professionals may not have access to on their own, whether identifying vulnerabilities or prioritizing threats by severity. With the constantly evolving online landscape, conducting a risk assessment can help a business keep pace with emerging threats.
Knowing how much exposure an organization has to certain risks and how to respond to them is key to preventing data breaches and other cybersecurity disasters. Taking the time for security risk assessments will pay off in the long run, as businesses can be more confident their most important assets are better protected.
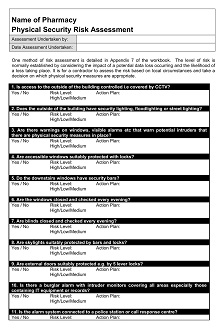
Assessing the Impact of Potential Vulnerabilities on Security
Security measures are always evolving and changing as cybercriminals become increasingly sophisticated in their tactics. Consequently, organizations must regularly assess vulnerabilities in their infrastructure and technology to preemptively combat new threats.
By identifying potential weaknesses beforehand and verifying these findings through targeted penetration tests, companies can identify ways to improve the protection of their systems before more malicious actors recognize security gaps. This proactive approach is one-way businesses can ensure their network defense capabilities remain strong and up-to-date.
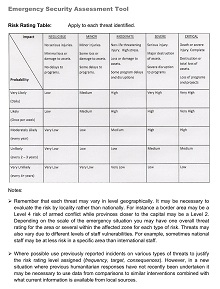
Essential Elements of Any Successful Security Risk Assessment Model
A successful security risk assessment model is integral to any comprehensive risk management program. It consists of several components, each of which must be properly addressed for the successful execution of a sound risk assessment process.
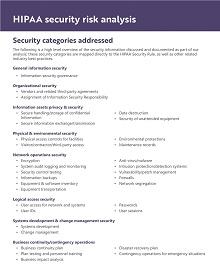
The essential elements include effective identification, asset valuation, risk categorization, threat assessment, analysis, and prediction to evaluate the likelihood of different threats’ occurrence, vulnerability identification and vulnerability-threat pair ranking, and control selection and implementation. Lastly, it is also important to consider compliance issues so that all regulations from relevant bodies remove any obstacle to successfully evaluating a security risk assessment model.
How to Create a Security Risk Assessment Template
The first step in creating a security risk assessment template is to define the scope of the assessment. For example, you should decide if this will be an individual project or if it will encompass multiple departments or locations within your organization.
Once you have determined the scope, you can gather relevant information such as existing policies and procedures, data storage and transmission software, backup solutions in place, etc. You should also gather any external reports about potential threats, such as cyber-attacks or other malicious activities that could affect your organization’s data security.
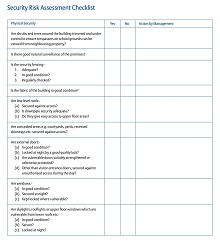
Once all this information has been gathered, it is time to create the template itself. You can use existing online templates or create one from scratch based on best practices for conducting a thorough risk assessment. The template should include sections for identifying potential threats and vulnerabilities, evaluating current controls and procedures for mitigating risks, assessing impacts if these risks become realized, and developing strategies for preventing future incidents. Additionally, it should provide clear instructions on documenting each step of the process so that you have detailed records available during any follow-up assessments or audits.